Introduction
This blog provides a deep dive into AWS's Identity and Access Management (IAM), a vital service for controlling access to AWS resources. We cover IAM users, groups, and roles, enabling specific permissions for interaction with AWS services. Gain a strong grasp of IAM's crucial role in managing user identities and access across AWS services.
IAM
IAM, or Identity and Access Management, is a core service provided by Amazon Web Services (AWS). It enables users to securely control access to various AWS resources within their accounts. IAM allows for the creation of users, groups, and roles, granting specific permissions to interact with AWS services, ensuring a secure and organized cloud environment. It plays a crucial role in managing user identities and their level of access across AWS services.
Let's discuss IAM Users, IAM groups, and IAM Roles.
IAM in AWS is structured around two main components: "Identities" and "Permissions."
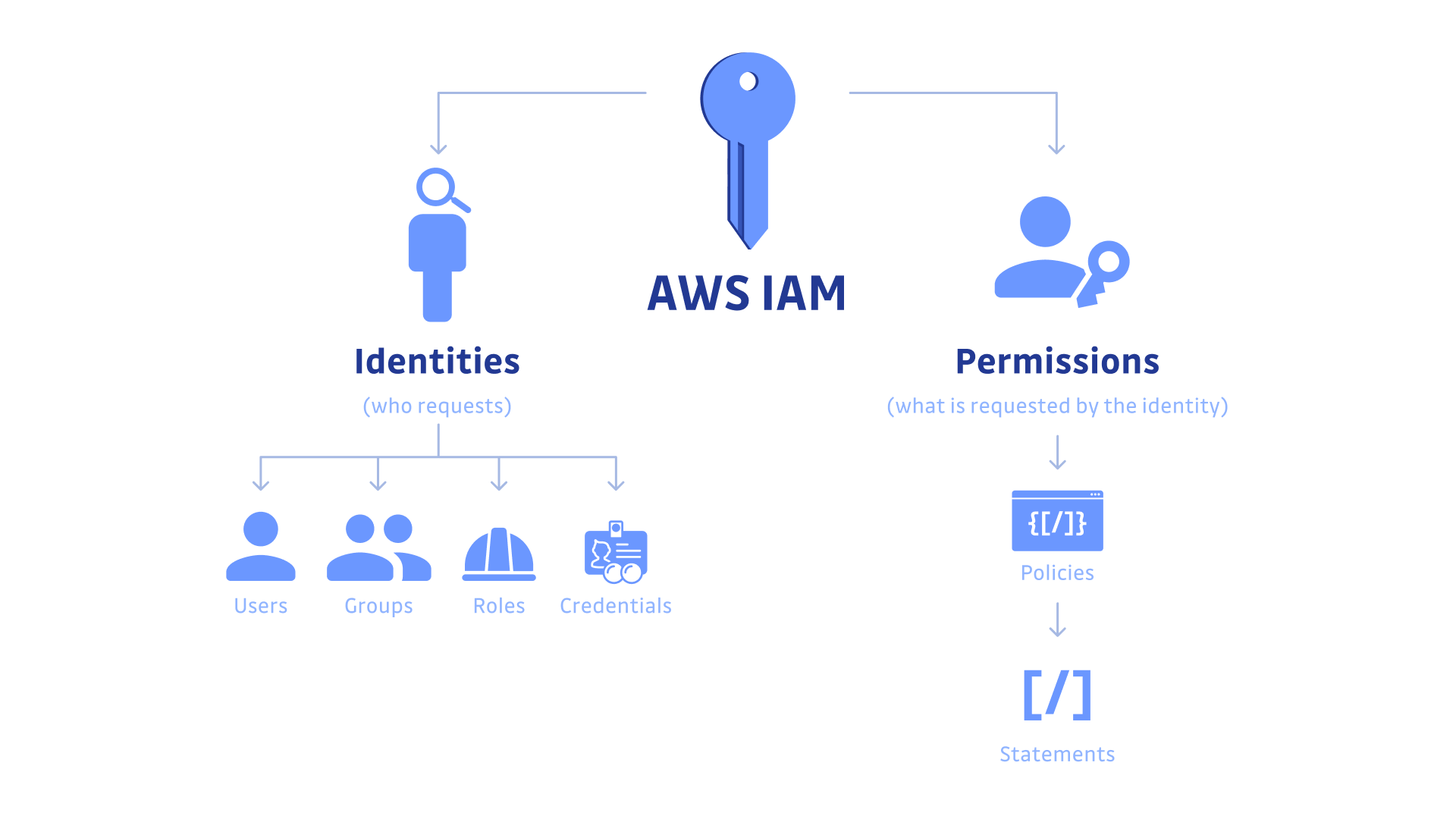
Identities: This encompasses the users, groups, and roles that exist within the IAM system. Identities represent the entities that interact with AWS services and resources.
Permissions: This defines what actions identities can perform on specific AWS resources. Permissions are set through policies and are associated with IAM users, groups, and roles, ensuring controlled access to AWS services.
IAM Identities: Users, Groups, Roles
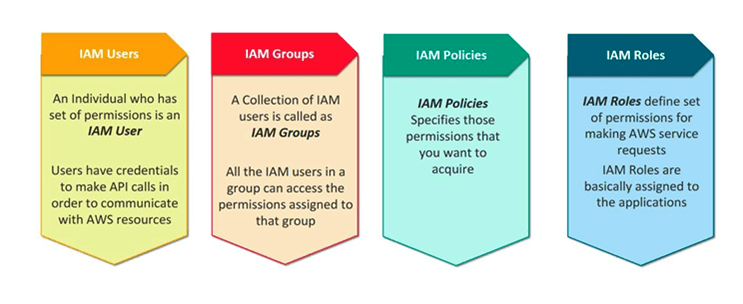
IAM users
IAM users in AWS are like individual accounts for people or services. They have their names and passwords or access keys. These users can do specific things in AWS based on the permissions they have. For example, some users can read files, while others can create new ones. It's a way to control who can do what in your AWS account.
When to use IAM users
You should use IAM users in AWS whenever you want to grant specific individuals or services access to your AWS resources.
IAM Groups
IAM groups in AWS are collections of IAM users. By organizing users into groups, you can apply policies to multiple users at once, simplifying permission management.
When to use IAM groups
Use IAM groups in AWS to efficiently manage permissions for multiple users with similar roles or responsibilities.
IAM Roles
IAM roles in AWS are sets of permissions that define what actions can be taken on which AWS resources. They are used to delegate permissions to AWS services, applications, or users from another AWS account.
When to use IAM Roles
Use IAM roles in AWS to grant temporary permissions for services, users, or accounts without the need for permanent credentials, enhancing security and enabling seamless resource interaction.
AWS User Data
User Data in Amazon EC2 is a powerful feature that allows you to automate the configuration of your instances during launch. It provides a convenient way to perform common setup tasks, install software, and execute scripts, making it easier and more efficient to get your instances up and running with the desired configurations.
By providing either shell scripts or cloud-init directives, you can customize your instances to suit specific requirements. This automation can save significant time and effort, especially when launching multiple instances with similar configurations.
Tasks:)
Task1:
Launch EC2 instance with already installed Jenkins on it. Once server shows up in console, hit the IP address in browser and you Jenkins page should be visible.
Access AWS Management Console:
- Log in to your AWS account and go to the AWS Management Console.
Navigate to EC2 Dashboard:
- Click on the "EC2" service to open the EC2 dashboard.
Launch an Instance:
- Click the "Launch Instance" button to begin the instance creation process.
Selecting an AMI:
- Choose a suitable Linux AMI that meets your requirements.
Configure Instance Details:
- Provide necessary details, including key pairs and security groups.
Advanced Settings:
Select advanced settings to customize the instance configuration.

Adding User-Data Script:
In the User-data section, insert a shell script to install Java & Jenkins on the server.
#!/bin/bash sudo apt update sudo apt install openjdk-11-jre -y curl -fsSL https://pkg.jenkins.io/debian-stable/jenkins.io-2023.key | sudo tee \ /usr/share/keyrings/jenkins-keyring.asc > /dev/null echo deb [signed-by=/usr/share/keyrings/jenkins-keyring.asc] \ https://pkg.jenkins.io/debian-stable binary/ | sudo tee \ /etc/apt/sources.list.d/jenkins.list > /dev/null sudo apt-get update sudo apt-get install jenkins -y sudo systemctl enable jenkins sudo systemctl start jenkins
Now, Launch the Instance:
- Complete the instance launch process.
Security Group Configuration:
Ensure that port 8080 (Jenkins default port) is open in the security group.

Connect to the Server:
Access the server via SSH and check the installed Java & Jenkins versions.


Verification:
Once the instance is operational, use the public IP to access the Jenkins page through port 8080 in your web browser.

Task2:
Create three Roles named: DevOps-User, Test-User, and Admin.
Open the IAM console.

In the navigation pane, choose Roles and then choose Create role.

On the Select trusted entity page, choose AWS service and then select the EC2 use case. Choose Next.

On the Add permissions page, search for and select the following permissions:
DevOps-User:AmazonEC2FullAccessTest-User:AmazonEC2ReadOnlyAccessAdmin:AdministratorAccess
Here I make only role for Devops-user

Attach Permissions Policies:
Search for and attach policies that define the permissions this role will have. For a DevOps-User, you might attach policies related to development and deployment tools.
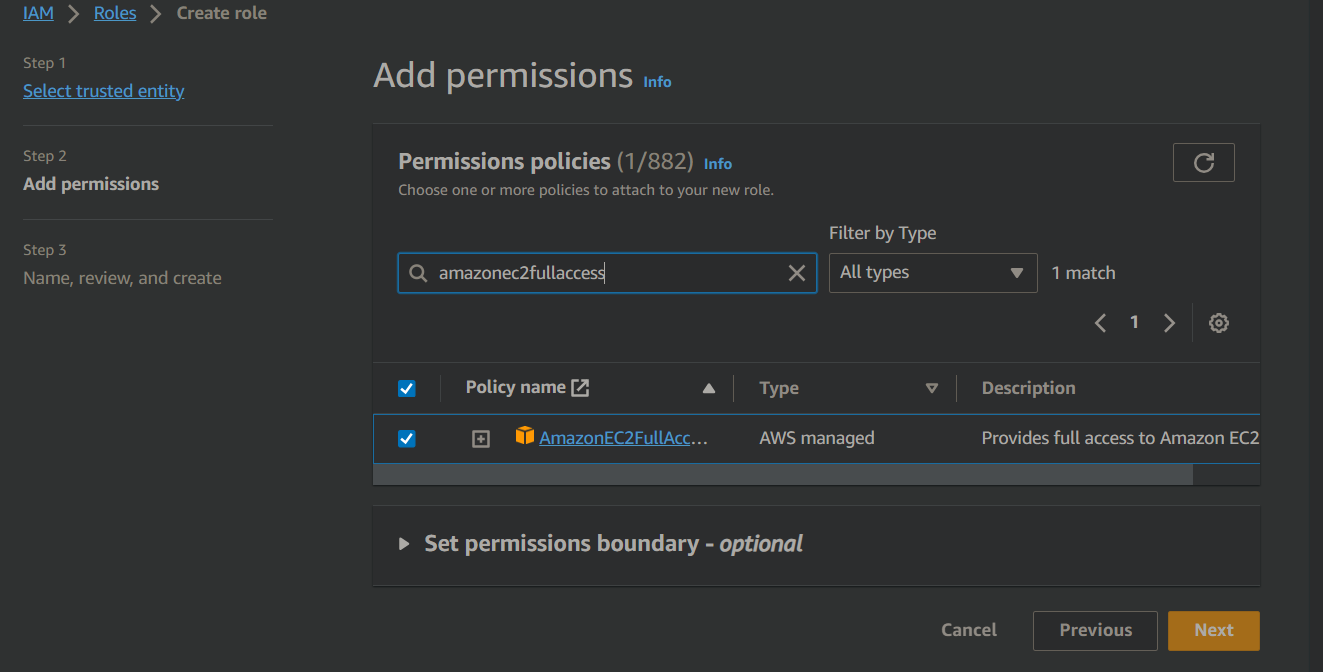
Review and Name the Role:
Give the role a meaningful name, such as "DevOps-User", and provide a description if desired.

Create Role:
Click on the "Create role" button.

Successfully created.

Repeat for Test-User and Admin:
Follow the same steps to create roles for "Test-User" and "Admin", selecting appropriate use cases and policies based on their responsibilities.
Test-User:AmazonEC2ReadOnlyAccessAdmin:AdministratorAccess
Conclusion:
You've delved into AWS IAM, a key service for secure resource management. IAM's user, group, and role framework empowers effective access control. A strong IAM strategy is essential for a secure and organized cloud environment.
Keep pushing boundaries in your cloud journey! 🚀
Thank you for diving into this blog with me! I trust you found the information both helpful and enlightening. To stay updated on the latest in DevOps 🚀, make sure to follow me. Remember, staying informed means staying ahead in the dynamic world of DevOps!
Feel free to connect with me on LinkedIn for more updates and discussions on DevOps 🚀
Happy Learning! Keep pushing those boundaries! 😊

